The Microsoft Cloud brings gives organisations the ability to manage and control end user devices in a flexible and secure way. Since the move to a more hybrid working model, organisations need to adapt and move to a more cloud-based management method.
Microsoft InTune allows IT Departments to manage and report on corporate and personal devices that are accessing company data, allowing users the flexibility of how they access the data whilst maintaining data sovereignty and security.
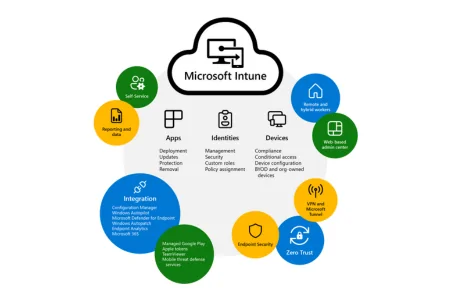
Microsoft’s Endpoint Management Provides

Microsoft’s Endpoint Management solution provides:
- Management of Windows, iOS, Android and MacOS devices
- Simplified app deployment and updates to managed applications
- Policy deployment for apps, security, compliance and more
- Self-service features to reduce overhead on internal IT resources
- Integration into other Microsoft Cloud solutions, such as Microsoft Defender, Autopilot and Windows Autopatch as well as other Third-Party solutions
Protect your Business Critical or Sensitive Data

Having the ability to protect your business-critical or sensitive data is vital to all organisations, once a device is enrolled into Microsoft Intune, you can:
- Create and deploy policies that configure security settings, set password requirements, deploy certificates and more
- Use threat defence services to scan devices, detect threats, and remediate threats
- View data and reports that measure compliance with your security settings and rules
- Use conditional access to only allow compliant devices access to organisation resources, apps, and data
- Remove organisation data if a device is lost or stolen
Application Management Policies
You can deploy Application Management Policies to end user-owned devices to:
- Use mobile threat defence services to protect app data by scanning devices, detecting threats, and assessing risk
- Prevent organisation data from being copied and pasted into personal apps
- Use app protection policies on apps and on unmanaged devices
- Use conditional access to restrict the apps that can access organisation email and files
- Remove company-specific data within apps
Find out more
Contact us to find out more.
