Email Phishing Attacks are on the Rise
In today’s climate, email and other electronic communication have never been so important. This has led to a spike in various groups and individuals trying to target users and businesses in order to steal their usernames, passwords, and credit card details to make unauthorised purchases, steal funds and even use the information they find to steal people’s identities.
For businesses, these attacks take a slightly different form but can still have devastating effects. These targeted attacks usually happen through emails, where malware is installed onto the network, which then finds its way onto servers where critical business applications and data are stored. These attacks take the form of what is commonly known as ‘Ransomware’ – meaning that the attacker will encrypt files, folders, and applications and only unlock them when the ransom has been paid. Previously organisations have paid anything from £500,000 to over £1M!
Now, it appears that attackers have gone one step further and are starting to bypass two-factor authentication systems. This means that now more than ever, we as individuals need to be more aware and vigilant when opening emails from external sources and websites that are asking us to log in with our organisation or personal credentials.
For those who would like to know more about the technical aspects, there are a couple of links from threatpost.com and confense.com which explain this in a bit more detail and tell you what to look for.
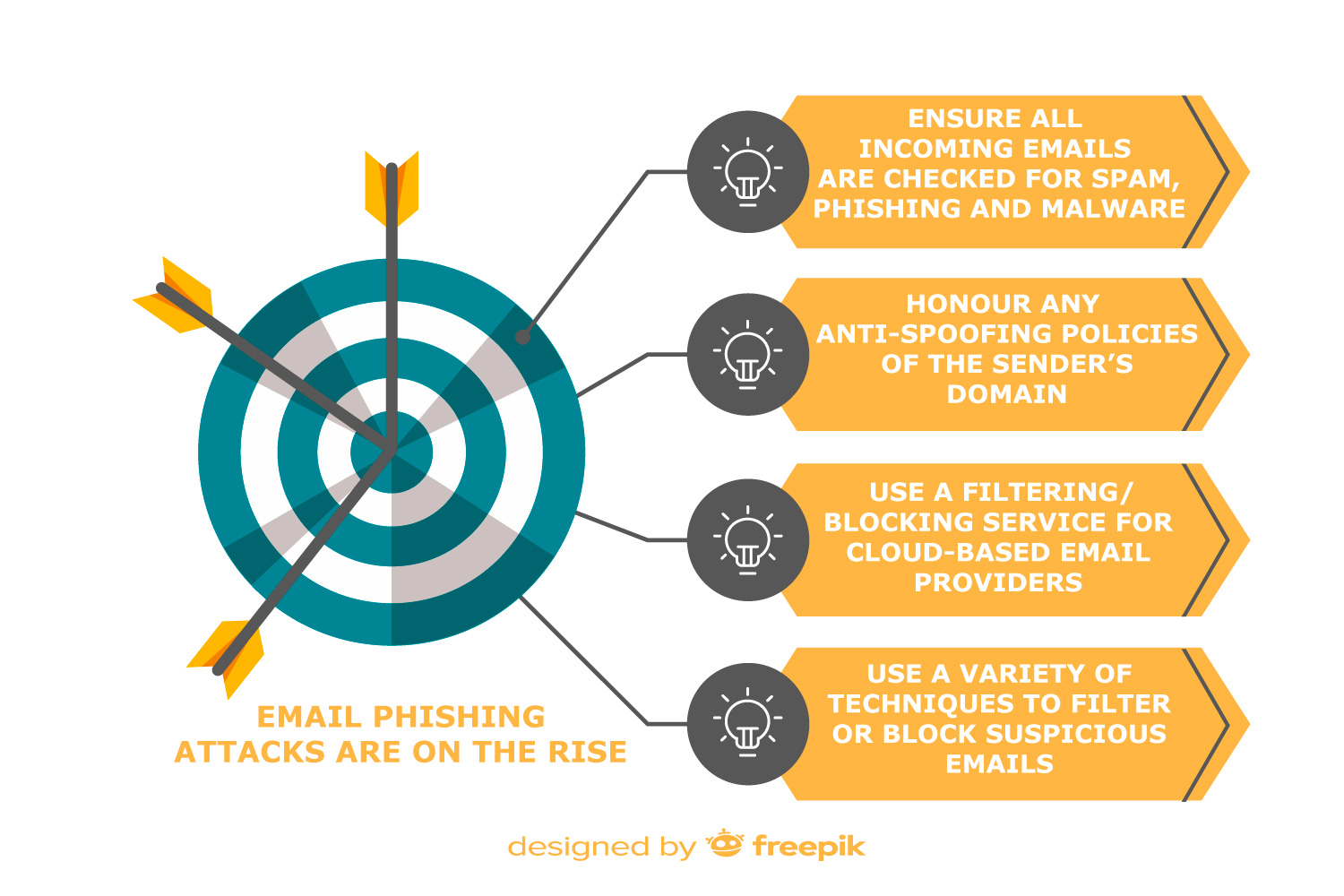
Your organisation’s I.T. department can look to implement some actions to protect your business from phishing emails, including:
- Ensuring all incoming emails are checked for spam, phishing, and malware. Any suspect emails should be filtered or blocked before they land in your inbox. This can be done on the server or in the mail client (end user device)
- Honouring any anti-spoofing policies of the sender’s domain. Spoofing is the forgery of email headers so that emails appear to come from someone other than the actual source. Anti-spoofing policies request for emails such as these to be quarantined or rejected.
- Ensuring that any filtering/blocking service used for cloud-based email providers, is sufficient for your organisation’s needs and that it is switched on by default. A balance needs to be found so that genuine emails are still able to get through and suspicious ones filtered or blocked.
- Using a variety of techniques to filter or block suspicious emails including IP addresses, domain names, email address white/blacklist, public spam and open relay blacklists, attachment types, and malware detection.
It’s not just the responsibility of the I.T. Department to protect the network and data. You as an individual can help protect your company’s data by being more vigilant when opening attachments and accessing links within the external emails you receive, especially when you are not expecting them. If in doubt, delete it and if you do click or login to anything you shouldn’t, contact your I.T. Department for assistance immediately. Taking these steps will help you to protect your organisation’s information as well as your own – which is more important now than it’s ever been, as cyber-crime becomes even more prevalent and advanced. If you would like more information about protecting your business get in touch with one of our experts about our Business Continuity and Disaster Recovery product.